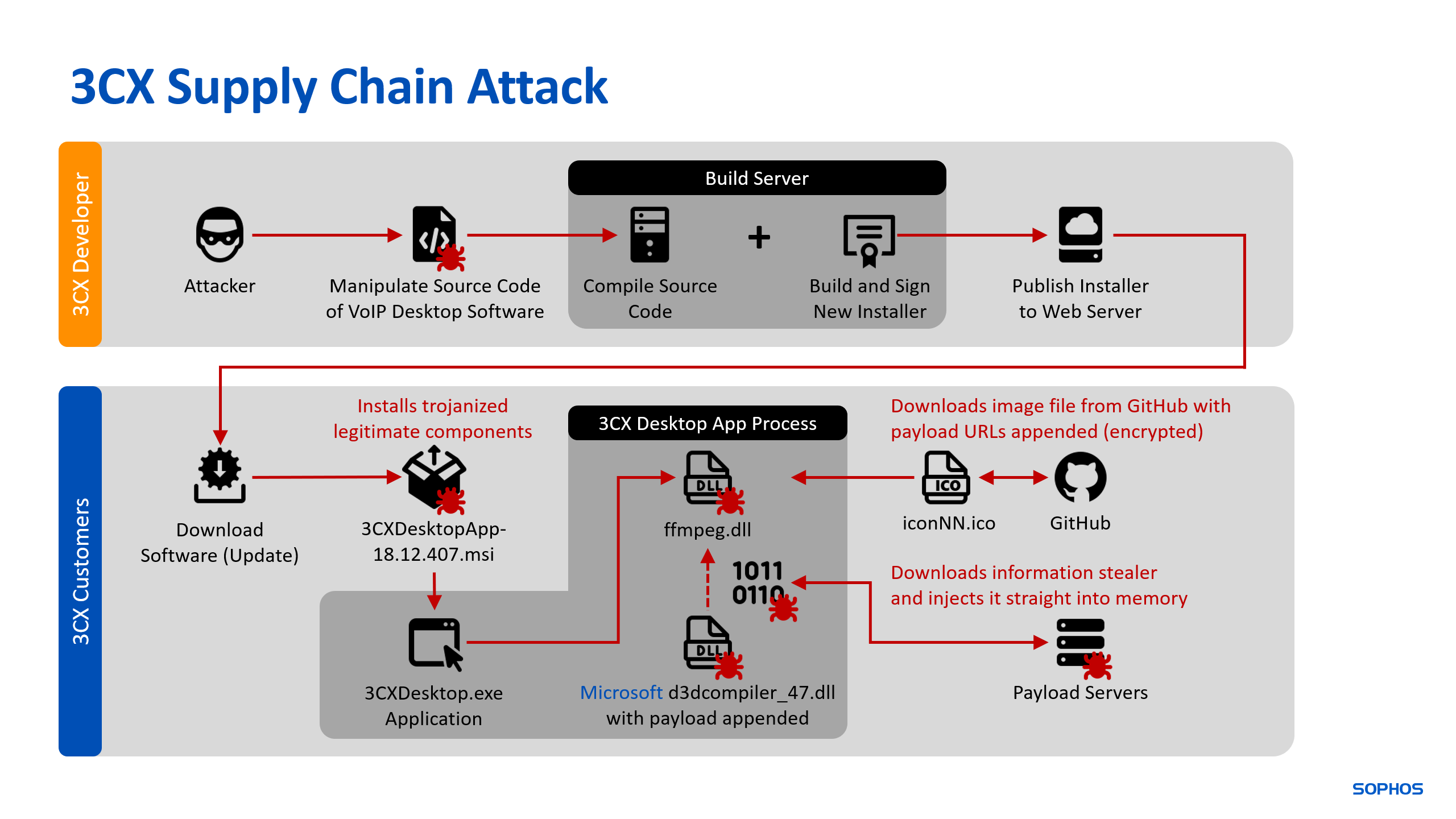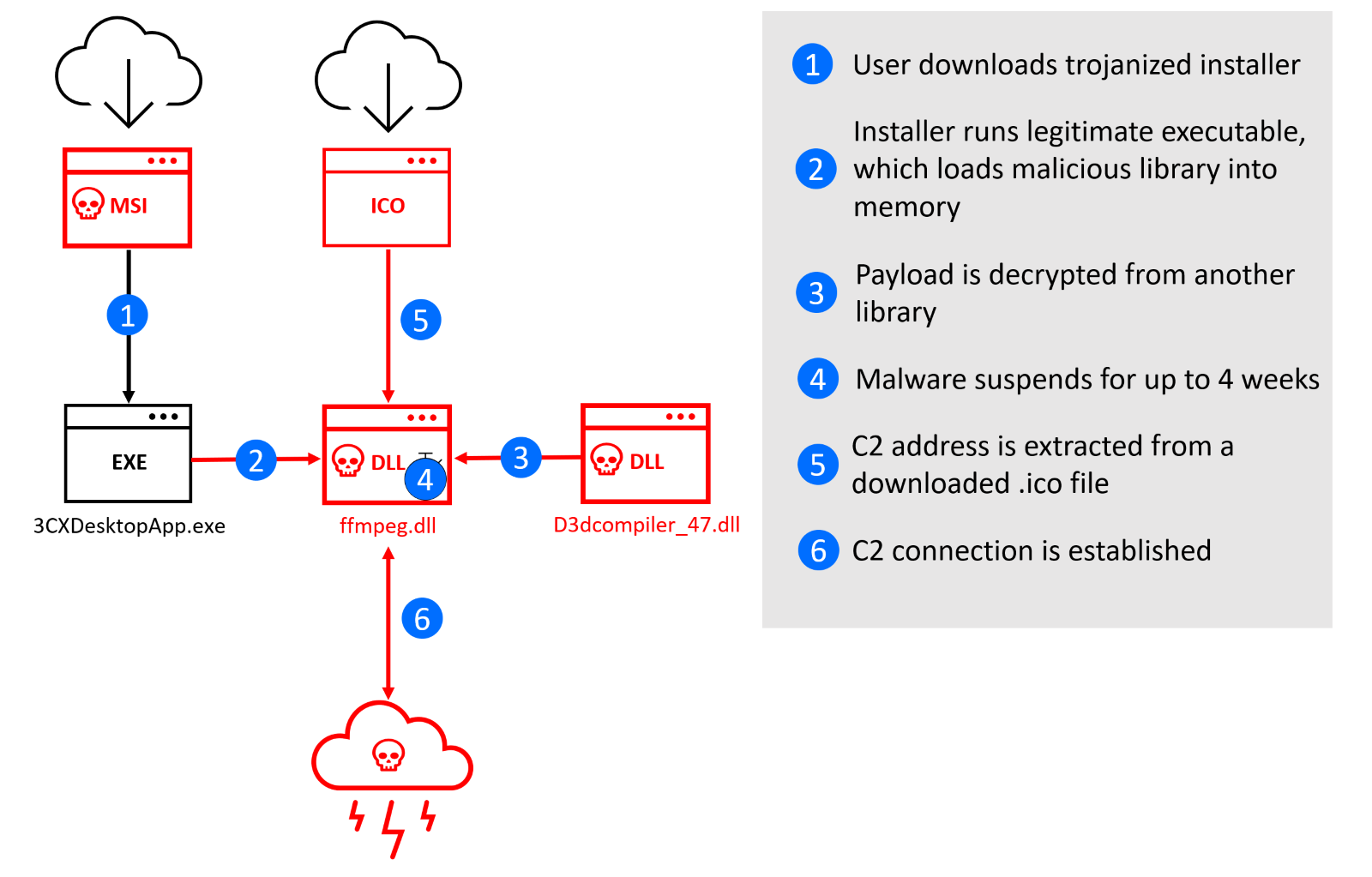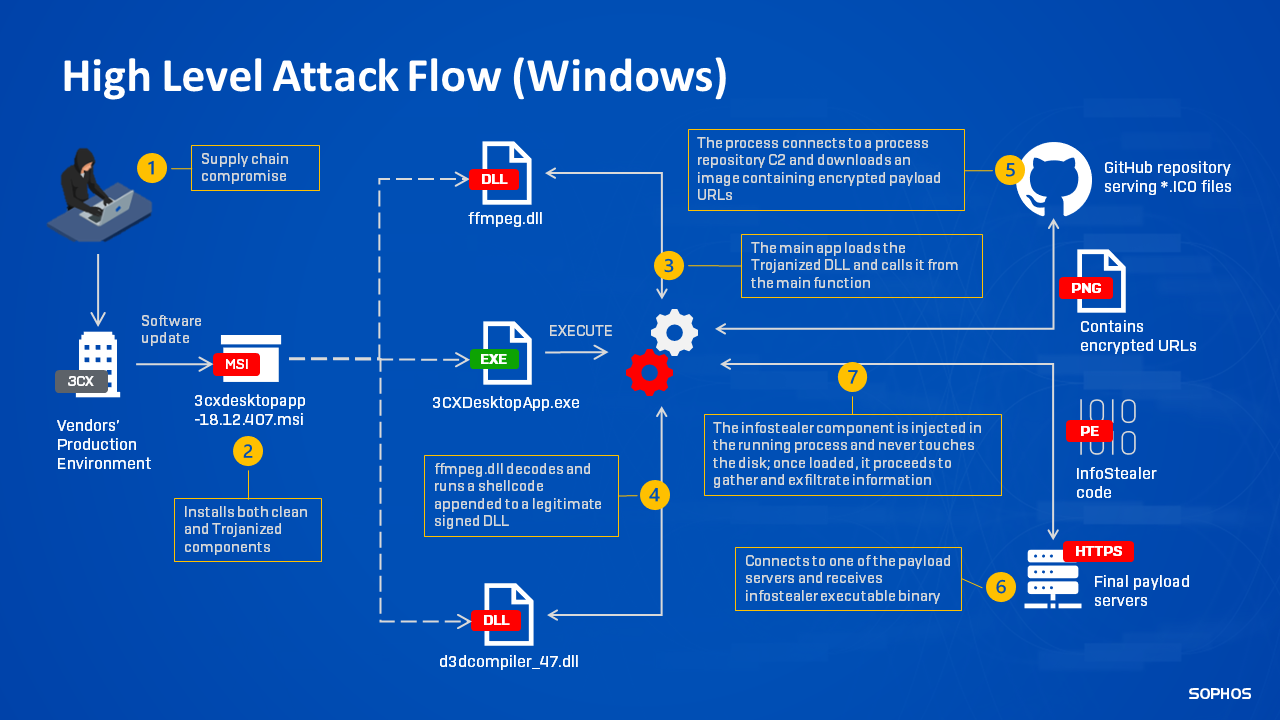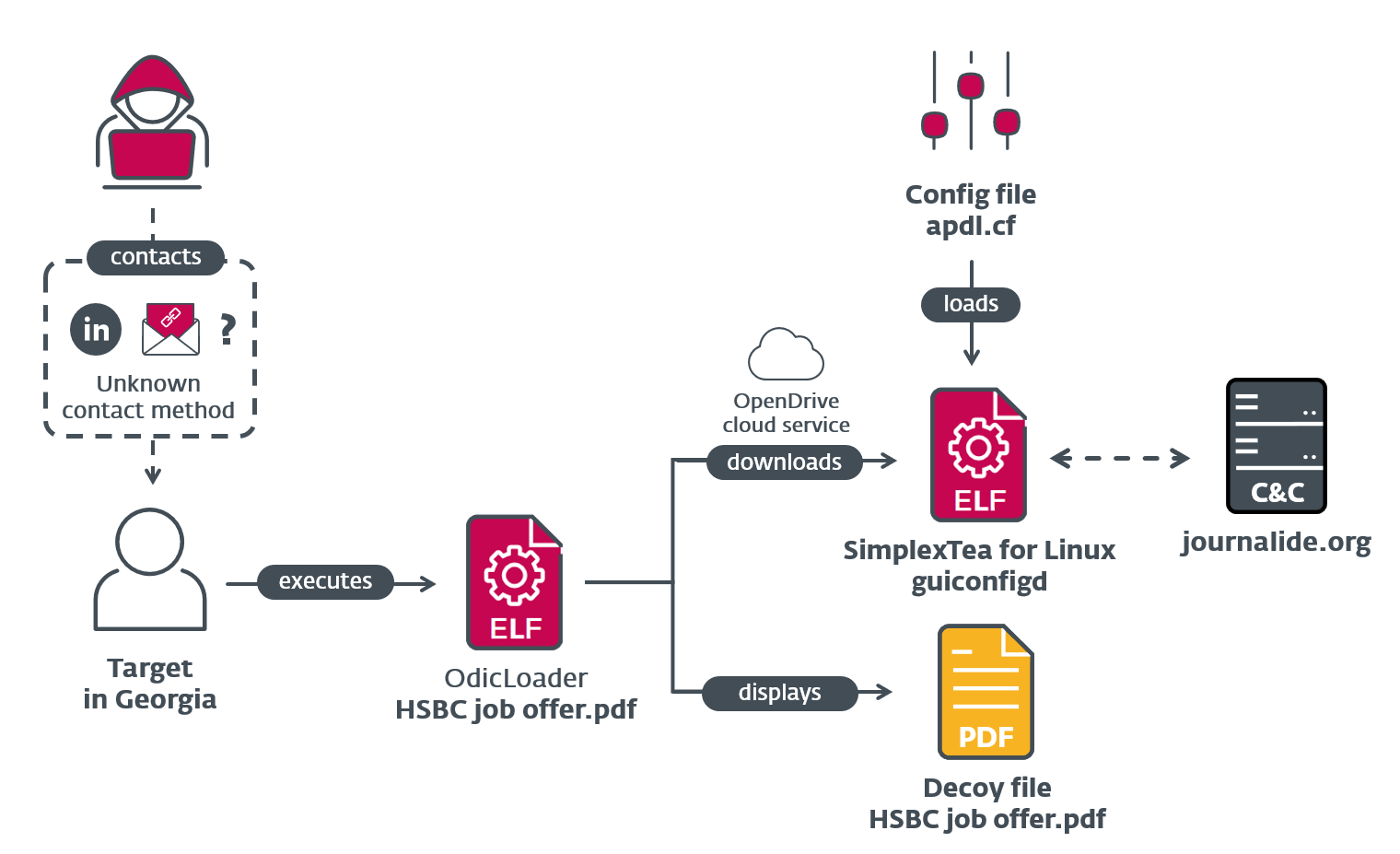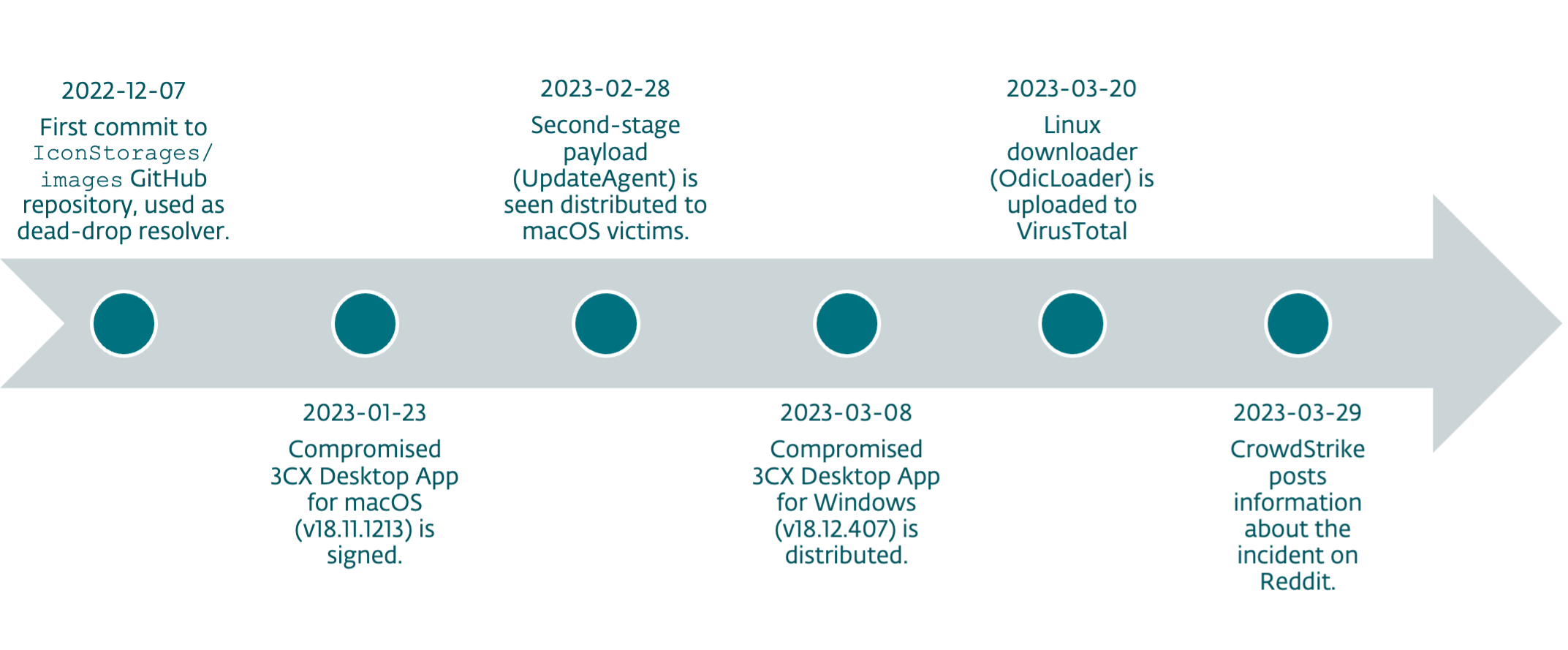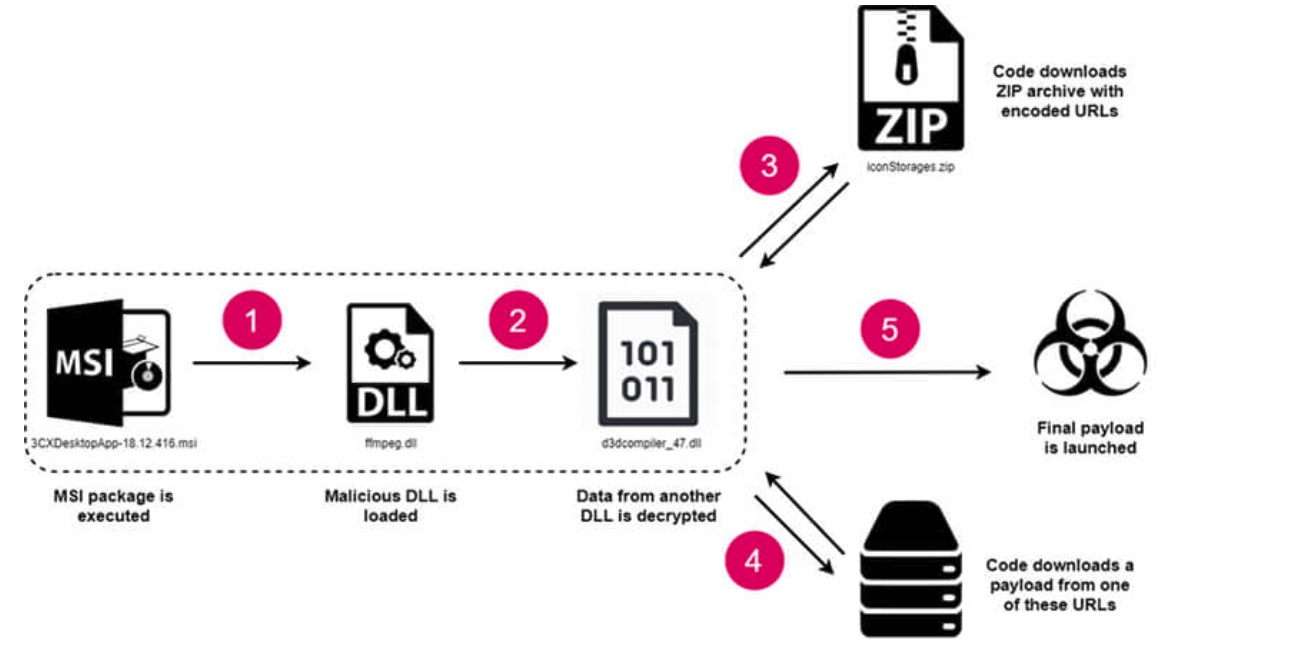
Trojanized Windows and Mac apps rain down on 3CX users in massive supply chain attack | Ars Technica
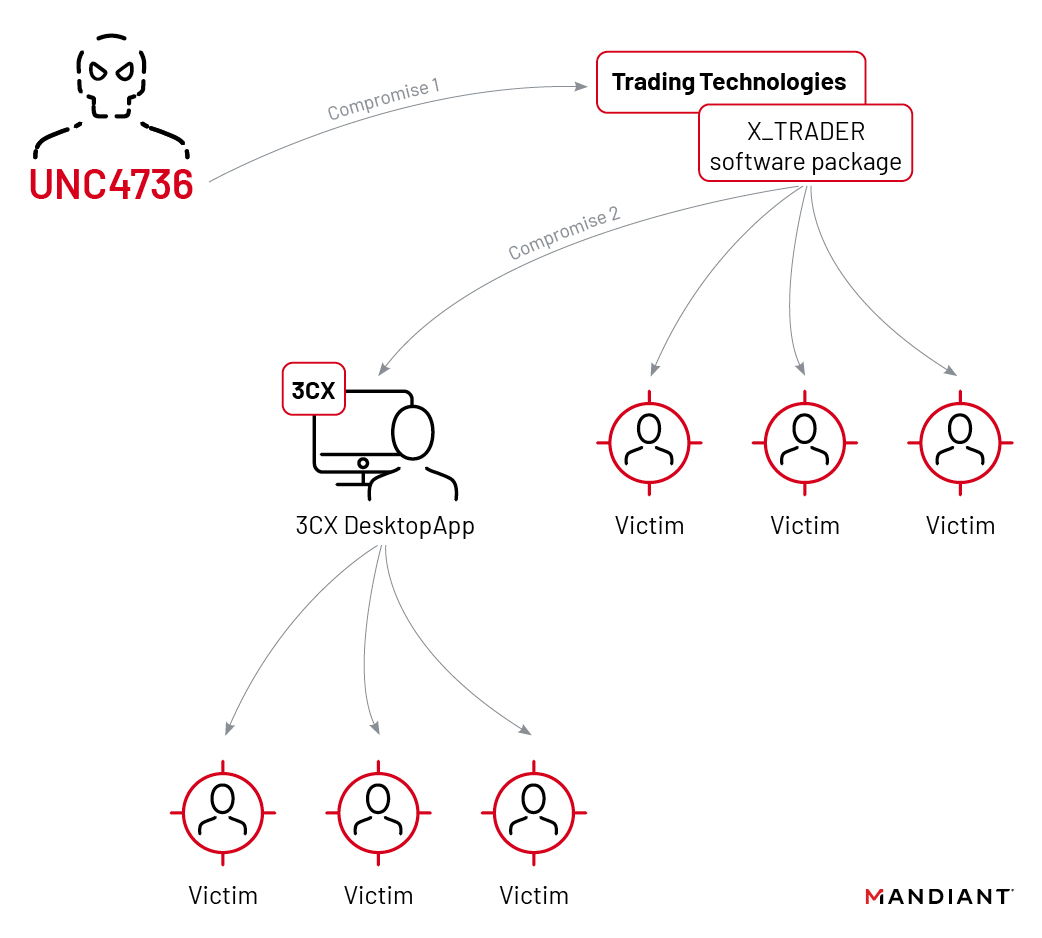
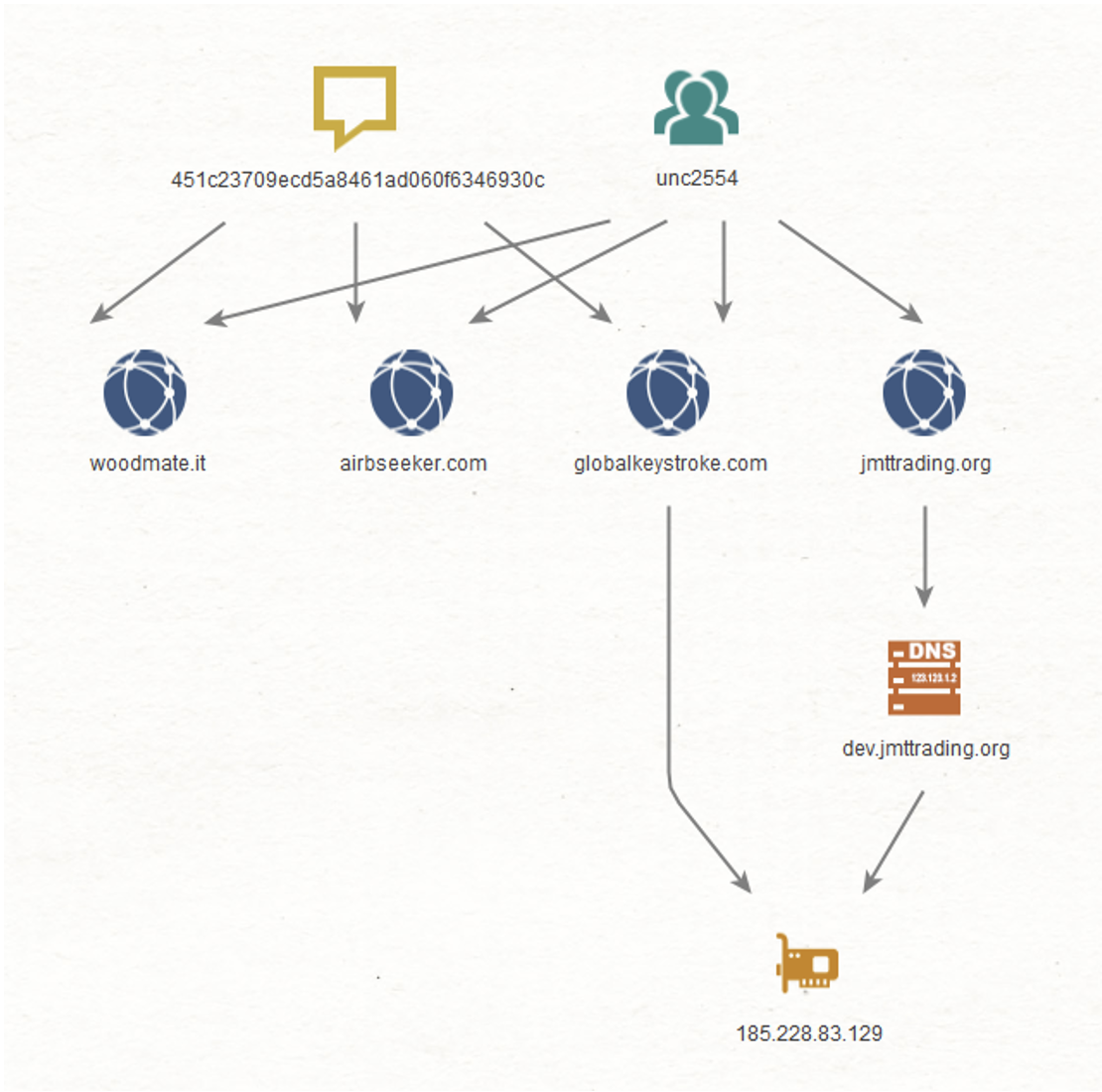
3CX Software Supply Chain Compromise Initiated by a Prior Software Supply Chain Compromise; Suspected North Korean Actor Responsible | Mandiant