JRC Publications Repository - Climate Vulnerability of the Supply-Chain: Literature and Methodological review

Supply chain vulnerability assessment: A network based visualization and clustering analysis approach - ScienceDirect
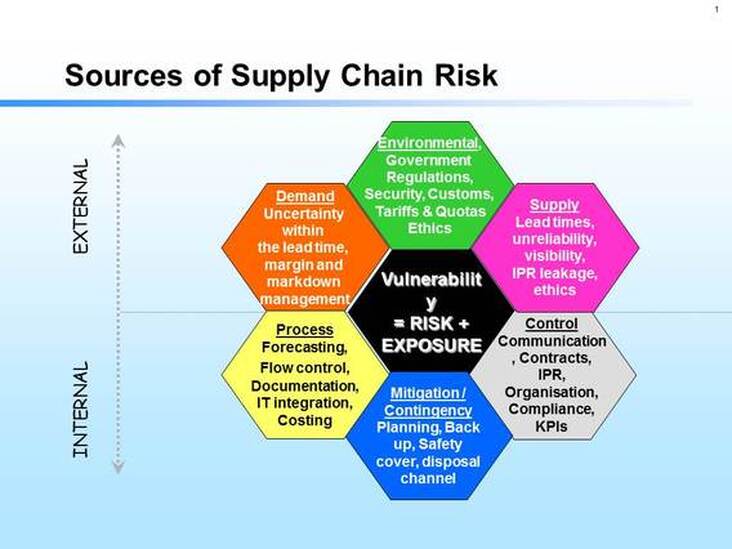
Supply Chain Vulnerability Map II Source: Adapted from Blos et al. (2009) | Download Scientific Diagram




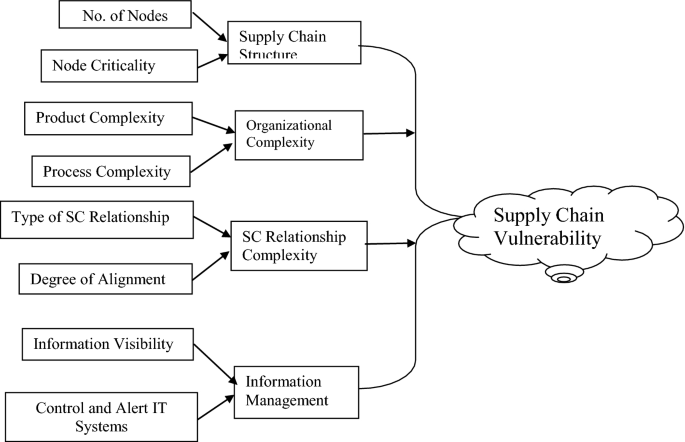
![PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar PDF] Assessing the vulnerability of supply chains using graph theory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c50328abeea3d9dea2146af86d1ca90996de067d/3-Figure2-1.png)
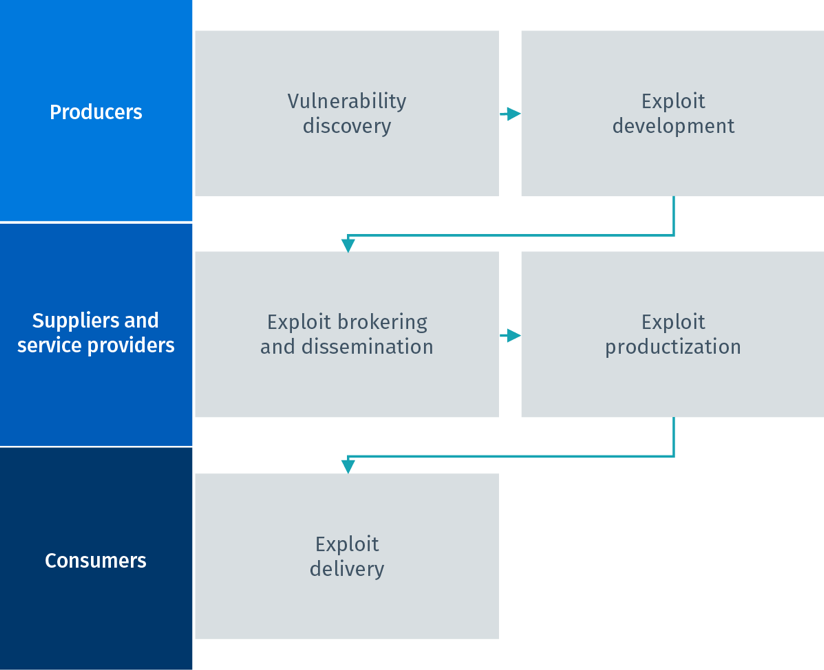
![PDF] An Integrated Method of Supply Chains Vulnerability Assessment | Semantic Scholar PDF] An Integrated Method of Supply Chains Vulnerability Assessment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0601698c6153d456dabe6e73b83a7cf6979dab38/3-Figure1-1.png)